Tag: IoT
Best Solutions and Technologies to Overcome IoT Security Issues
Why IoT security is so critical
IoT devices can be made secure using various techniques, standards, and tools to protect IoT systems from data breaches, leaks, and unwanted monitoring. Currently, IoT application security is one of the top priorities of any company that benefits from this technology.
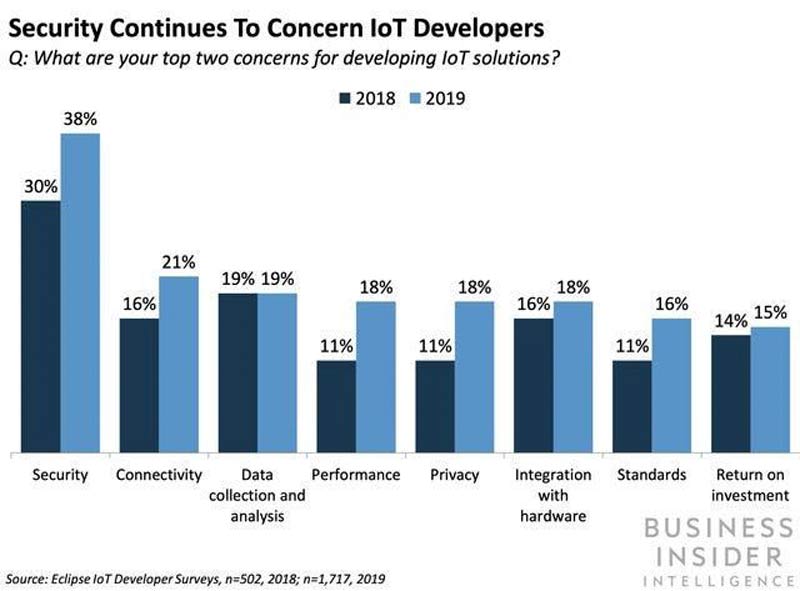
According to an F-Secure report, cyber-attacks on IoT devices grew by 300% from 2018 to 2019, reaching 2.9 billion events per year.
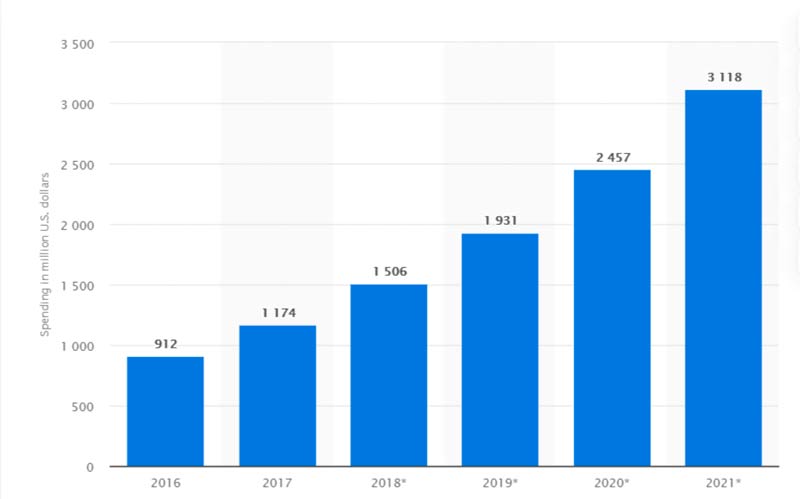
It’s no surprise that the amount of money companies spend on cyber security in IoT also increases each year. According to Statista, in 2021, companies worldwide will spend over $3,118 million on device security.
According to a MarketsandMarkets report, the value of the global IoT security market will increase from over $6 billion in 2017 to $29 billion by 2022.
So why is it so hard to maintain security for IoT devices? Let’s talk about the main IoT security issues and challenges.
What are the challenges with IoT security for developers?
IoT systems face many challenges that slow down their development and adoption:
- Insufficient regulation
- No industry standards
- Vulnerabilities due to human factors
- Unreliable passwords
- Legacy assets and IT systems
- Cost of maintaining security
Let’s talk about these IoT security challenges in more detail.
Lack of regulation. Manufacturers rarely make their devices with security in mind. In some cases, devices can even ship with malware that infiltrates the whole system. Certainly, there are IoT security companies and guidelines — for example, OWASP for the Internet of Things — but at the end of the day, manufacturers aren’t obliged to follow them. However, lack of regulation is still one of the biggest challenges for secure IoT.
No industry-accepted standards. Often, devices lack security because developers and manufacturers simply don’t know what a secure IoT system even means. There are no standards in the IoT industry, so everyone interprets security differently. This also slows down the adoption, as many devices from different manufacturers are incompatible because they use different protocols.
Human factor. Despite all the efforts companies make towards protecting their software from hackers, the majority of data breaches happen as the result of an action by someone who has access to the system. This action could be setting a weak password, downloading a file from an untrusted source, or simply opening a link or file that contains malware. Educate your employees and monitor their activity to prevent breaches.
Unreliable passwords. Often, IoT devices have preset passwords that are very easy to crack. But the new passwords users set often aren’t reliable either. Make sure all your devices are protected by unique and complex passwords.
IoT security is costly to maintain because you need to replace assets, use expensive tools, get certification and conduct penetration testing regularly
Legacy assets and IT systems. A business’s legacy assets and IT systems probably weren’t designed to be integrated with IoT devices. Because it’s costly to replace every asset, existing hardware is often equipped with small sensors that may be vulnerable due to old software that hasn’t been updated for a long time.
Cost of maintaining security. Maintaining security is a complex and never-ending process, as hackers come up with new ways to break into the Internet of Things systems every day. You need to perform regular checks, get IoT security certification, conduct penetration testing, and use specific and usually costly tools to check your software for vulnerabilities. Because security is costly to maintain, many companies fail to do so.
However, all these challenges can be overcome with a good team of specialists who know exactly what tools and technologies to use in order to ensure the safety of an IoT system.
14 steps you can take to secure your IoT devices
The main advice for security is to know all the ins and outs of your infrastructure — including all devices and servers — and monitor their statuses. Most importantly, remove or update anything that’s old. As simple as it sounds, this is really hard to do, however, as organizations are still figuring out how to track their devices and evaluate vulnerabilities.
1. Build your infrastructure with security in mind. Security starts with the design of your network architecture. Your developers should assess vulnerabilities at the start of the project. Every project should be well-documented, and documentation should be updated each time the team adds or removes something from your infrastructure. Also, use devices that have been certified, for example by CTIA IoT Cybersecurity Certification Program.
2. Never use hardcoded credentials. Most hacker attacks that succeed do so because of weak credentials. Even if you sell devices with default credentials for convenience, you should make sure the user immediately sets their own strong password. Back this up with two-step authentication or biometrics for better protection.

3. Think about your API safety. An API can become an entry point into your system for hackers, so be sure to regularly check the security of your APIs. It’s essential that only authorized devices can connect to your back end through an API so data sent from devices to servers can’t be manipulated.
4. Ensure physical security. When we think of IoT security, it’s usually about software. However, it’s just as possible to corrupt a system through hardware. You should make your devices tamper-proof and make sure they’re able to withstand harsh conditions.
5. Identify each device. You should be able to quickly identify issues with each particular device, so put unique identifiers on each of them to learn what data they send and how they work.
6. Use digital certificates. Digital certificates help with identifying public encryption keys, exchanging data securely, and setting up identity verification. Public key identification or PKI-based certificates protect device-to-device and device-to-server data transmission. To make your certificates effective, pair them with security protocols.
7. Use encryption. Encryption is crucial for the security of any software, whether it’s a mobile app or an IoT system. There are several encryption methods:
- Data Encryption Standard (DES)
- Advanced Encryption Standard (AES)
- Triple Data Encryption Standard (Triple DES)
- Rivest–Shamir–Adleman (RSA) encryption
- Twofish encryption
8. Segment networks. As technologies evolve, networks become bigger, and it’s a challenge to control all devices at once. To help with this, divide a large network into segments and restrict access to each segment so that a data breach in a small part of the network won’t affect your whole system. Each segment should be responsible for all activity that happens inside it, detect any anomalies, and immediately report them.
9. Protect your network. After you segment your network, it’s time to properly protect each segment: use antimalware tools and firewalls, block IP addresses that aren’t authorized, use cryptography and take care about your port security. You should also make sure your network systems are up to date, and use IoT security solutions to increase your system’s safety. Think about cloud IoT security, as you will probably use cloud storage in your ecosystem.
Use antimalware tools and firewalls, block IP addresses that aren’t authorized, use cryptography and take care about your port security
10. Integrate security gateways. Gateways will work as a buffer between your devices and the network, allowing you to keep hackers from your system and implement firewalls.
11. Set up automatic updates. It’s a challenge to manage devices and their software and not lose track of updates. To make sure you never forget to update your software, you need to automate updates.
12. Educate your team. Most security breaches occur as the result of an action by a user, so educate your employees and set up security rules everyone should follow. Your staff should also continuously learn about new frameworks, systems, architectures, and so on. Train your staff on new types of threats and security methods.
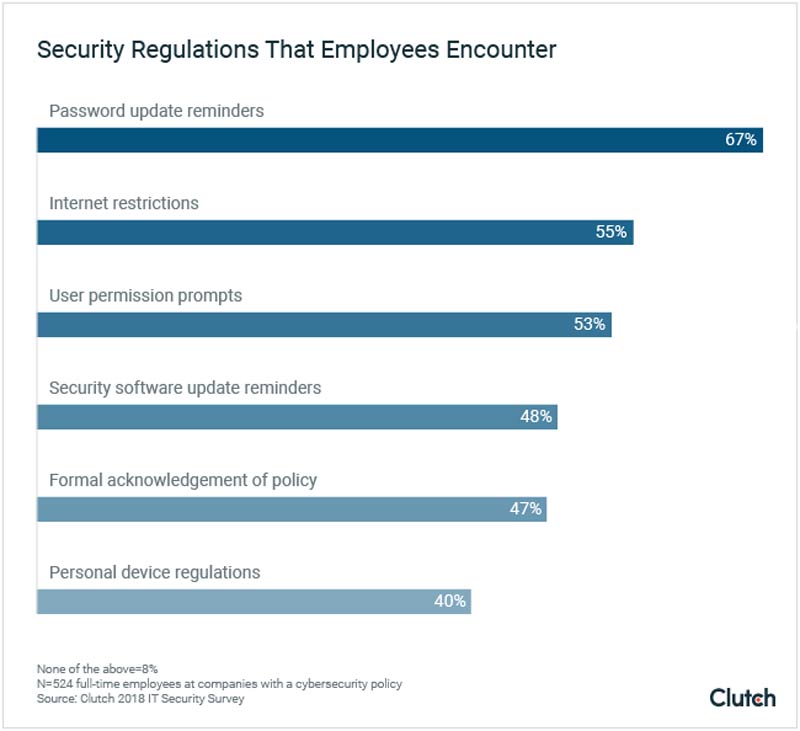
13. Educate your users. If you’re planning to sell your hardware and software to end users, you should educate them as well. Warn users about possible dangers of IoT systems and smart home systems and require them to change the default credentials.
14. Test your system frequently. You need to constantly run tests that emulate real-world situations. For example, if you have an IoT-based industrial security system with different sensors for temperature, smoke, humidity, etc, you need to regularly check if they’re working right so that in a critical situation you’ll be able to act on them effectively. Also, to perform penetration testing, you can use IoT security tomography and a layered attacker model: it allows you to identify vulnerable parts of your software and model the possible attacks.
IoT security legislation
Governments also care about security and privacy in IoT, so there are a few laws and regulations you should take into account when you create a system. They provide rules, checklists, and recommendations for implementing safe IoT services.
In 2017, Congress passed a law that prohibits any IoT device sold in the US from using default passwords. This and other requirements were introduced in the IoT Cybersecurity Improvement Act.
If your target market is the EU, you should pay attention to the GDPR. Though it’s not IoT-specific, it protects user data and establishes rules by which manufacturers and developers should ensure IoT device security.
In 2018, California approved an IoT security bill SB-327 on information privacy, which contains a list of requirements for all IoT devices sold within California.
5 best IoT security technologies and tools
IoT network security
It’s a bit harder to implement network security for IoT devices than for other types of hardware because devices use many different protocols and don’t have clear standards.
To make your network secure, you should use common antivirus and antimalware programs along with firewalls and malware detection systems.
Authentication
Only legitimate users and devices should be able to get access the network, so you need to implement authentication. To implement authentication in your system, you can use:
- MAC (Message Authentication Code)
- PKI
- OAuth2
To identify users, you can use:
- Username and password
- Tokens
- Biometrics
- Two-factor authentication that combines the methods mentioned above
To secure your IoT/M2M (machine-to-machine) endpoints, use these types of identification:
- RFID (radio-frequency identification)
- Shared secrets
- X.509 certificates
- MAC addresses
Security analytics
Security analytics uses telemetry data from IoT devices to analyze and detect anomalies in an IoT ecosystem. To implement analytics, you’ll need to deploy massively parallel processing (MMP) to process large amounts of data in real-time.
MMP is then combined with analytics, allowing you to detect anomalies in real time. You can also set up rules: for example, to let the system automatically shut down if it detects a threat or to block all access to untouched components of your infrastructure.
You can also use AI and machine learning to derive valuable conclusions from all the data you collect.
Here are some top companies that offer IoT analytics products:
- Cisco
- Indegy
- Kaspersky Lab
- SAP
- Senrio
Encryption
Encrypt all data at rest and in transit between devices and servers using cryptographic algorithms. Here are the most popular encryption algorithms for IoT:
The Data Encryption Standard uses the same key for encryption and decryption, which the sender and receiver share.
The Advanced Encryption Standard is more secure than DES and uses one encryption key of different lengths, re-encrypting data from 10 to 14 times.
Triple DES is flexible and compatible with many IoT systems, but though it’s still in use, it’s considered obsolete and is not recommended by NIST.
RSA encryption uses public key encryption technology that allows users to share data without sending code to the recipient in advance.
The Twofish encryption algorithm was offered as a substitute for AES. It uses a single key of any length up to 256 bits. Twofish works great on low-capacity computers and IoT smart cards.
Third-party IoT services and tools
If you use any third-party services, tools or frameworks for your system, make sure they correspond to all security standards. Solutions from Intel, Microsoft Azure, Senrio and Ericsson are certified, so you can use their open source materials for your own ecosystem.

One example of such services is Verizon IoT security credentialing. It’s a set of tools and services that helps to maintain devices. Verizon offers three protection layers, data encryption, device authentication, etc.
How to provide security to IoT devices: final thoughts
IoT technologies are extremely complex but will eventually become a part of almost every aspect of our lives. Currently, there are lots of businesses, enterprises, factories, and individuals who are enthusiastic about IoT and are integrating IoT technologies into their operations and daily lives.
However, there are some factors that prevent IoT from spreading faster, and almost all of them are in one way or another connected to security concerns. Because of the complexity and a lack of regulations and standards in this domain, IoT devices are currently one of the easiest for hackers to enter.
To prevent IoT security breaches, you need to constantly update your software, perform testing, and use encryption, firewalls, and data protection algorithms. Investing in the education of your employees and users will also pay off.
If you want to create a secure IoT system, make sure your software developers follow the best practices of end-to-end security in IoT. We are currently working on a power bank sharing startup that has IoT technology at its core.


