Tag: temptag
11 Web Application Security Best Practices You Need to Know
Why care about your web app’s security?
Everything that has access to the internet can be hacked, from computers to small IoT devices. And since even the smallest devices track personal information nowadays, they’re a gateway for hackers to get sensitive data about millions of people. According to Forrester, three sectors account for the majority of successful cyber attacks:
- Government
- Retail
- Healthcare
These sectors are the most popular among hackers; however, if your web application or website is in another domain, it’s not a reason to relax. If your database stores information about your users, that’s reason enough to protect your software and eliminate any security issues.
According to Corero, a single DDoS attack can cost a company around $50,000 in lost revenue. Losses in the case of a security breach include not only the personal data of your users but, more importantly, users’ trust in your business. And lost trust leads to even more significant financial and reputational losses.
There are many types of cyberattacks. Here are some of the most common:
- Cross-Site Scripting (XSS)
- SQL Injection
- DDoS Attack
- Malware
- Bots
- Cross-Site Request Forgery (CSRF)
- Broken Authentication
- Exploiting inclusion vulnerabilities – LFI and RFI
So what is web application security? It’s all the strategies, tools, and technologies you should use to prevent these attacks from compromising your code and your clients’ private data.
In this article, I’ll be talking about application security best practices. I’ll talk about overall cybersecurity strategies and small things that make a difference.
Common web app security vulnerabilities
Before we discuss how to fight vulnerabilities, let’s find out where they come from and where you need to look for them. There are ten most common security vulnerabilities in web applications according to OWASP:
- Injection flaws – attacker uses malicious data to attack the databased and directories of your web app
- Broken authentication – a hacker gets access to user profile by hacking the credentials. It can be easily avoided with multifactor authentication
- Sensitive data exposure – hacker can easily get access to data that’s not protected with encryption
- Missing function level access control – a hacker can attack the backend of your app if the server-side authorization is misconfigured, broken or non-existent
- Security misconfiguration – include unpatched flaws, unused pages, unprotected files or directories, outdated software, and running software in debug mode
- Cross-site scripting XSS – a hacker gets access to a web app by planting the malicious code into links that a user needs to click to initiate the attack
- Insecure direct object references – exposed database files or keys open lots of vulnerabilities. Hackers can try to get these files by using enumeration attacks
- Cross-site request forgery – hackers trick users to click the links with malicious code and take over their sessions
- Using third-party components with vulnerabilities – your web app can be hacked through vulnerabilities from the third-party components you use in your product
- Unvalidated redirects and forwards – a hacker forwards a user to a malicious website where they can steal user’s data
Most of these vulnerabilities are the result of issues with authentication, user input flaws and validation of data, so it’s important to prevent these issues by protecting your authentication and validation mechanisms. Any web app development services should include security strategy and regular security checks during and after development along with other best practices of web security.
11 best practices for web security
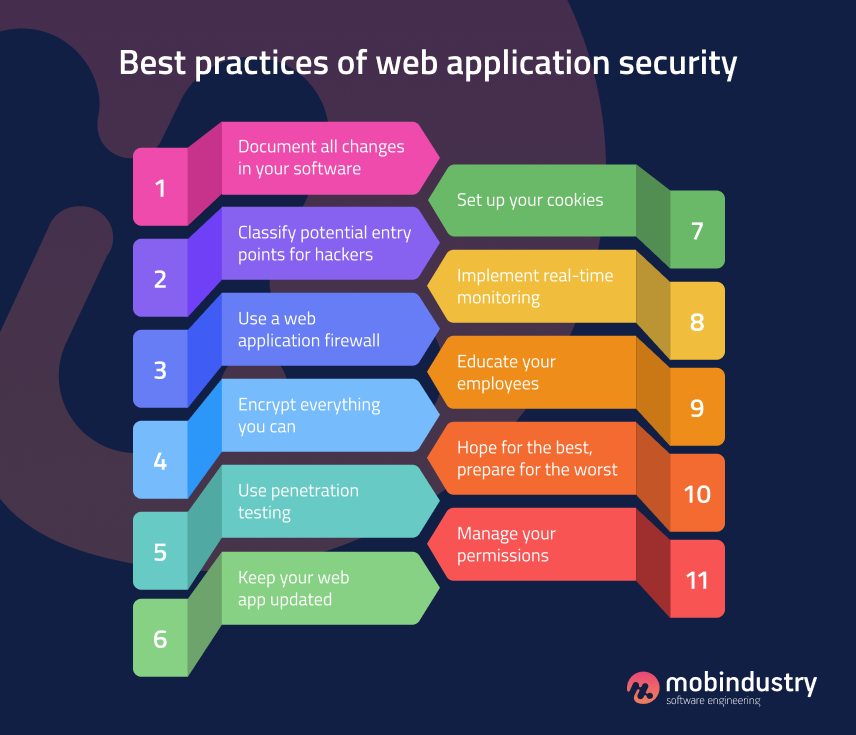
1. Document all changes in your software
The first point of our web application security checklist doesn’t seem so difficult at first, because it’s always easier to find something in a room where everything’s in order. In real life, however, there’s never time to get organized. It’s the same with software: once your web app goes live, the number of new features and changes grows.
A single breach in a third-party library can cause a major data infringement incident
While chasing ever-changing requests from users and trying to keep up, software developers and owners put off documenting changes to the software and risk their web security. From a security standpoint, this is a huge mistake that can cost a company quite a lot.
As your project grows and evolves, developers add new frameworks, libraries, and features. A single breach in a third-party library can cause a major data infringement incident in a company, and without documentation, it will be very hard to find where the problem occurred.
2. Classify potential entry points for hackers
Some parts of your software are more vulnerable than others because they’re customer-facing and handle data transactions. To make sure you focus on making web application security checks in the right places, divide your software features into modules according to security priorities:
Critical modules – contain the most vulnerable, customer-facing features that are the closest to the internet. These are the most attractive entry points for hackers. Examples include login screens and checkout pages.
Serious modules – involve parts of the software that store sensitive information about the company or its users.
Normal modules – Normal modules don’t have direct access to sensitive information in your app but also require attention and constant checkups.
3. Use a web application firewall
A web application firewall (WAF) is basically a filter for HTTP traffic between a server and a client. It doesn’t let any malicious requests go through and infiltrate your databases.
Firewalls are one of the most popular ways to protect software at the entry points to your network, as they analyze all incoming traffic and stop all suspicious activity. WAFs don’t require developers to change anything in the source code, which also makes them convenient to use.
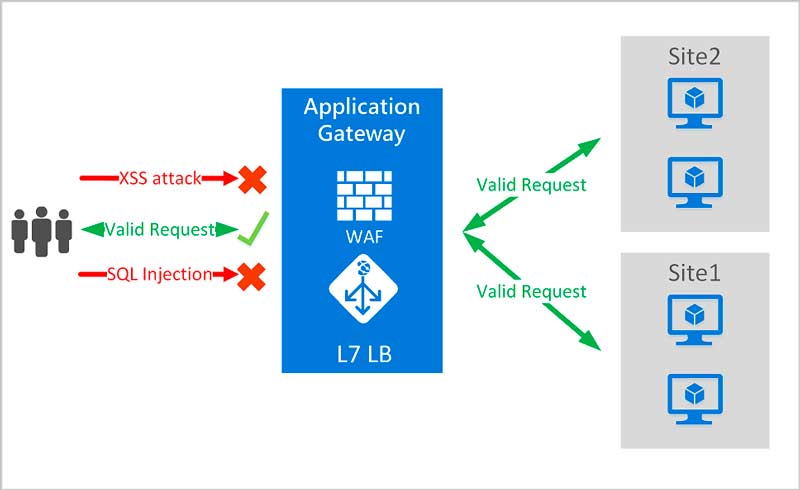
However, traditional firewalls have their drawbacks: they can’t detect some types of attacks. To ensure maximum security, use advanced WAFs that can protect your application from SQL injection attacks and cross-site scripting.
4. Encrypt everything you can
Use basic technologies like HTTPS and HSTS encryption, but don’t stop there.
Implement SSL encryption for all user data you send to and receive from the server. While HTTPS is great and makes man-in-the-middle attacks nearly impossible, it’s not enough if somebody has access to your server.
This somebody can be anybody, from a system administrator to a former employee. To keep your data safe even when someone has access to it, you need encryption and hashing.
5. Use penetration testing
Penetration testing is one of the most advanced parts of any security testing. It puts your software in near real-world situations where a QA specialist plays the role of a hacker and tries to infiltrate the system by any means, from programming to physical violation.
Penetration testing allows you to effectively find most vulnerabilities and results in a detailed document that can serve as the basis for a security check and a reference when finding the vulnerability that caused a breach. Penetration testing offers several techniques to make sure all situations are considered.
If you want to know more about penetration testing and its results, read our article on this topic:
There are over ten possible reasons for software vulnerabilities, and a regular web app of medium complexity has dozens of entry points, such as cloud access, that can be used by hackers. This is what penetration testing is for: it allows a QA to play out lots of scenarios and try to infiltrate the system with as much knowledge of it as a hacker would have in a real-world situation.
If you don’t have expertise in penetration testing, it’s a good idea to hire an expert from another company. A third-party professional will not only test your web app but conduct a full security audit of it while performing penetration testing.
Auditing your software with the help of an outsider often allows you and your employees to see flaws you didn’t know existed.
6. Keep your web app updated
When I talk about updating your web application, I don’t mean only your software but all the third-party services and libraries you use in its infrastructure. Hackers often use third-party software to infiltrate the main system, so beware of these threats as well. Here’s where your web app’s documentation will help a lot.
Many developers hesitate to update third-party services for their software, and this may lead to major breaches
Look at your documentation and see what libraries you use. Get rid of ones that don’t actually make any difference to your app and update everything that remains. At the very least, build an update strategy, as updating libraries sounds easier than it actually is. Many developers hesitate to update third-party services for their software because newer versions may lack backwards compatibility and mess up the whole system.
To avoid vulnerabilities that are present in any framework or library, you should:
a) Make sure you actually use all the libraries integrated into your software
b) Use the latest version of each library, if it’s stable
7. Set up your cookies
Almost all websites use cookies, and they’re necessary for both website owners and users. Websites use cookies to get information about users, which provides them with more insightful analytics, and users get a faster and more personalized experience on the website in return.
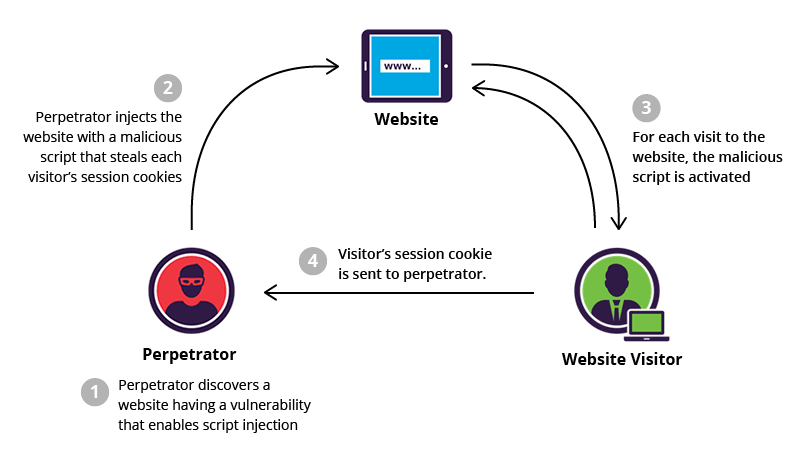
However, cookies can be a way for hackers to get in, so be sure that your cookies are safe. There are three main concerns when it comes to the security of cookies:
Information stored in your cookies — make sure it’s not sensitive. Don’t store passwords in your cookies; otherwise, hackers can easily get them and enter your system from another user’s account.
Expiration date — don’t make cookies last forever. Cookies should expire in less than a month, so request authorization every two weeks or so. This will make your web app more secure and you’ll know for sure that it’s an authorized user who is entering the app each time.
Encryption — encrypt all the information you store in cookies for more reliable security.
8. Implement real-time monitoring
According to the Ponemon, it takes around six months on average for a company to detect a security breach, even if it’s major. If you store lots of sensitive data, your priority is finding any breach and eliminating it as soon as possible. For this, you can use special monitoring software that detects all actions your employees take on their work computers. This can help you make sure all the security requirements are met.
According to Chief Executive, 90% of all security breaches are made possible because of human error. Monitoring your employees will allow you to quickly find out what action on which computer compromised your system, since everything will be on the record.
9. Educate your employees
We’ve already spoken about human error, and it’s more common if people don’t know where exactly they can make a mistake. If you have a big organization, it’s easy to lose track of what your employees deal with in different departments on a daily basis.
While you can always monitor employees, it’s more effective to prevent a security breach than to hastily search for the cause after an incident has occurred. Educate your employees on how to use software securely and what actions can lead to data infringement. Teach them what to do in case of a data breach and develop security standards that control their actions. To do that, you’ll need to take the next step.
10. Hope for the best, prepare for the worst
Have a plan for when a data breach happens.
According to the Ponemon Institute, 70% of companies don’t have a plan in case of a cyber security incident or a strategy for securing web applications. This leads to:
- Slow response to cyberattacks
- Significant losses of time and money
- Loss of trust from both employees and clients
Your plan should contain a classification of attacks, and for each type it should have a list of actions and a time frame within which they should be completed. Not only should you have an emergency plan, you should also test it regularly to make sure your systems work properly and your employees react quickly and effectively.
To make your response to threats more effective, you can automate most response activities by using:
- Identity management tools
- Authentication technologies
- Incident response platforms
- Security information and event management tools
11. Manage your permissions
Limit access to your software according to employees’ needs. Create a permission level grid to provide your employees with permissions they need for their work.
If your own employee decides to harm your company, you’ll also be sure that they can’t access any sensitive data through their own account
Giving workers different levels of access to your system has two main advantages. First, if someone breaks into your system through an employee’s credentials, you’ll make sure they can’t go any further than what the system allows.
Second, if your own employee decides to put your company in a difficult situation, you’ll be sure that they can’t actually access all sensitive data solely through their own account. Blocking your former employees and changing passwords after a developer leaves the company is another web application security best practice.
Quick suggestions
These are some other suggestions you may find useful:
- Use an encryption service (e.g. Let’s Encrypt) or buy an SSL certificate to redirect all your HTTP requests to HTTPS.
- Implement an x-xss-protection security header to defend your web app from cross-site scripting.
- Use strong passwords since simple, short, and predictable passwords are the primary way for hackers to infiltrate your system.
- Define approved content sources with the help of a web app content security policy. This will prevent your website from loading any files from a potentially malicious source.
Final thoughts
In this article, I’ve shown you how to secure web applications.
Follow these eleven web development security best practices if you want to keep your business and reputation free of malicious hacker attacks. Of course, nothing can guarantee security 100%. However, you can significantly decrease the chances of a data leak.
To do this, you need to keep your software in order: document all changes and make sure that all third-party modules, libraries, and frameworks you use are up-to-date. To protect the data inside your databases, you should definitely encrypt it. This way, hackers won’t be able to make any use of it even if they get to it.
It’s also a good idea to pretend to be a hacker yourself and perform penetration testing on your code. This will allow you to test your web application in real-world situations and audit your code.
And, of course, don’t forget about your employees: they should know what to do in case of a hacker attack and should be aware of human errors that can enable an attack. Educate your employees on secure behavior to minimize the chance of a mistake.
If you feel like you could use a web app security audit of your web application or a penetration testing report, be sure to contact Mobindustry. We’re a mobile and web development company with a business mindset, and we view web application security as one of the vital factors for any business’s success.


